
Ghidra Stack String Explorer
15 Aug 2024 - FoundryZero
We have released a Ghidra plugin to make finding and reading stack strings easier, and better integrated with other string analysis
Get it here: github.com/foundryzero/ghidra-stack-string-explorer

The problem
Thanks to compilers being compilers, or deliberate obfuscation, it is not uncommon for strings to be stored across instruction immediates rather than nicely all in one piece. These strings can then be rebuilt on the stack at runtime (hence the name) but may also be constructed elsewhere or only compared against other variables and not directly touch other memory locations. This makes finding the strings difficult, and reverse-engineering tools like Ghidra often present you with a long string of hex that’s hard to read and harder to search for.
The solution
So we bring you Stack String Explorer.
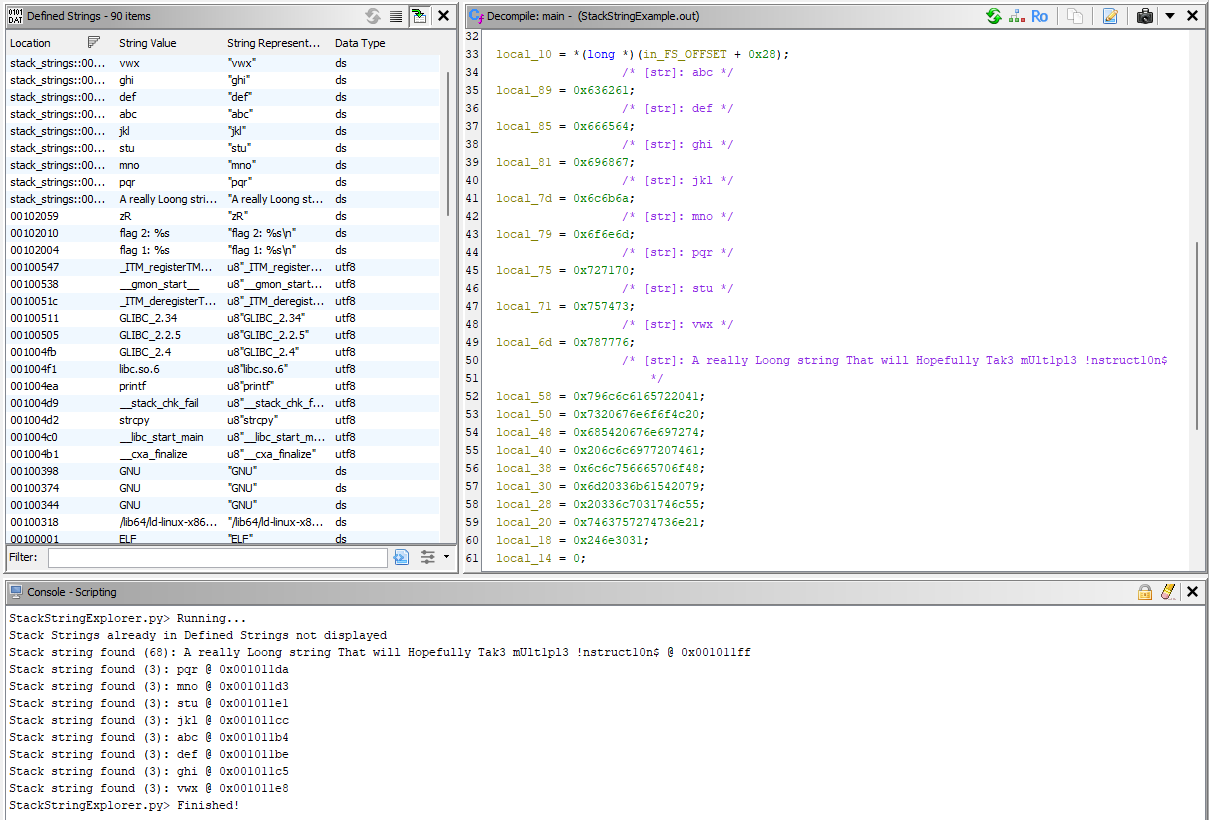
Stack String Explorer searches through targeted binaries, finding constant strings and reconstructing their different components to recover the full string.
It then presents comments in the relevant sections of the decompilation and listing views, displays the full list of discovered strings and their locations to the console, and, perhaps most importantly, adds the strings to the defined strings window so they can be searched and filtered along with all other strings in the binary.
Other useful features
- Variable scope - can target single functions, a specific selection, or set to run over all functions at once
- Headless support - runs just as well in headless mode, with settings provided in a
.propertiesfile - Grouped repeated strings - stack strings that appear multiple times have a central point with cross references to all uses of the string
- Address filtering - filters out printable characters that originate from constants that are likely to be addresses to reduce false positives
How it works
By default, Stack String Explorer works by simulating snip-its of instructions around an immediate that contains printable characters, following through where each constant is moved and used to finally extract strings from memory modified by the snip-it. This allows the tool to infer which string components are related, what order they should be reconstructed in, and whether any characters are overlapping across components.
In Simple Scrape mode Stack String Explorer will instead discard any information about how a constant is used and concatenate together string-like constants used by nearby instructions. This results in a more reliable, brute force approach without all the bells and whistles of simulation and falls more inline with other tools like SimpleStackStrings.
Join in
Stack String Explorer is open source, and pull requests are welcome. Please make sure suggestions are well formatted and described, but other than that feel free to submit any feature requests or other contributions.

